Cloud Security
Introduction
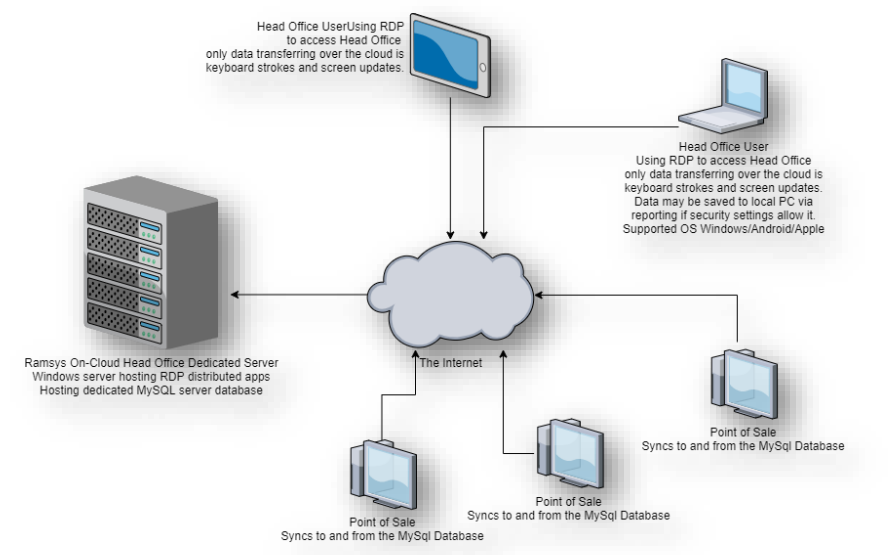
Ramsys Head Office Evolution is the most comprehensive Retail Management System available.
It is generally and preferably installed on the cloud on servers provisioned and maintained by our very experienced technology partners on their Cloud platform. While the issue of Data Sovereignty is simple, you own your data, no exceptions the security of your data is paramount to us and it belongs to you.
To this end the approach is multilayered and taken very seriously by both our partners and Allspoke. Each customer has a separate database rather than a single store, this ensures your data is segregated.
The following outlines the basic standards and extra disciplines offered to increase security.
Database minimum restrictions
The Database used by Ramsys HO is MySQL Vsn 8 with the following minimum standards.
- Each store will access the server via a unique username and password
- Passwords are minimum length of 10 which must include letters (both upper and lower), numbers and at least 1 punctuation character. Passwords are not words found in a dictionary but a random sequence of the accepted characters
- Root or SA access will not be granted to anyone. At the customers request a superuser can be setup for the Ramsys Database.
- Data transmission uses a compressed protocol rather than text. Full SSH encryption is available if required but due to the overhead/risk factor not set by default
- Database privileges are strict and set to the minimum required to perform the required tasks of each application.
- The use of Symlinks to tables is disabled to prevent malicious file deletions
- Access to the database is only available by default to the secure compiled Ramsys applications. Application may be made to provide access to the company or third parties at the companies request. Procedures for making these requests are available on request.
- The database access credentials are held within Ramsys POS and HO they are encrypted using AES. Encryption is performed in volatile RAM, decrypted credentials are never written to disk or other forms of non-volatile RAM.
- Due to the enhanced security capability available access to the server is only allowable via the Version 8 or higher drivers.
- All installation history and test databases are removed to prevent any possible exploitation regardless of how remote
- Features disabled to further tighten security include
- Limited ability to the SHOW DATABASES command o Disabling of the LOAD DATA LOCAL INFILE command
- At the customers request we will obfuscate the root account
- At the customer request we can change the default port mapping (external ports are not set to the default)
Enhanced Security Options
It is possible to increase the protection provided with your data access to the MySQL database.
- Limit access by IP address. While this requires the use of a Static IP by enabling this feature it is possible to only allow access from certain PC’s.
- Increased password policy is available to suit the company’s policy structure. RAMSYS HEAD OFFICE EVOLUTION Cloud Security 3
- A password policy that states that 2 incorrect logins will lock an account for 24hrs. Allspoke staff monitor this event. At the Customers request this may be made more stringent.
The preferred method of Hosting Ramsys HO is on the cloud through our technology partners. This relationship stretches back to 2006 and has resulted in a strong, best of breed yet practical solution which balances security and availability with performance and ease of use.
Unlike other clouded solutions Ramsys is provisioned via a browser by using strict RDP protocols for logging in. This provides a very fast, secure connection.
By default no direct access is allowed to the data or the server increasing the security against attack by magnitudes. Ramsys Central is available on any device with an HTML browser whether it be Windows/Apple/Android or Unix.
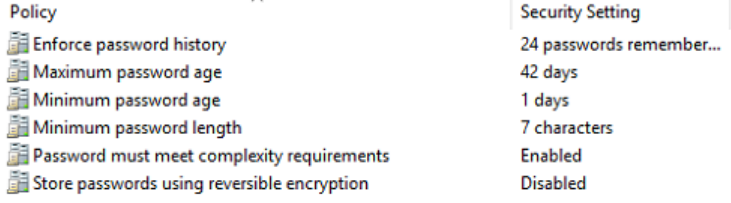
Default Password Policy
The following is the default password policy, this is able to be customised if required to match customer policy.
Full Virtual Environment
Our cloud partners on request can provide full RDP access to your application on a dedicated server. Contact us for detail.
Monitoring
All servers are monitored using connect-wise automate and Liongard Customer dashboards may be setup to provide customer specific KPI’s on server health. BIT are also subscribers to ID Agent which provides Channel-focused Dark Web monitoring and the most validated credential exposure data available.
ID Agent's sophisticated intelligence allows customers to focus on their business with peace of mind (https://www.idagent.com/
Backup
Backup is performed in 2 forms, your entire dedicated server is backed up using Datto backing up to a Sirus S4XE36E.
The Datto backup solution provides a wide range of powerful features integrated into a single data protection platform.
- All-in-one solution – The Datto Agent, Datto Device and Datto Cloud are all proprietary Datto systems that work seamlessly together in a fully integrated platform. The solution is owned and maintained by Datto, and there are no third party vendors involved.
- Image-based backups – Datto uses image-based backups to capture a complete snapshot of a protected server. The Datto Agent uses Microsoft’s Volume Shadow Copy Service (VSS) to take copies of open files well as SQL databases and Exchange mailboxes. In a recovery situation, images of protected servers can be restored to new hardware (bare metal restore) or can be converted to HyperV or VMWare virtual machines.
- Flexible Backup Schedules – The flexible scheduling tool on the Datto Device can be configured to perform backups from once a week to every 5 minutes. The scheduler allows the selection of hours of the day and days of the week, so backups are performed based on the customers business requirements.
- Screenshot Verification – At the end of each day, the Datto Device automatically virtualises the last backup image and performs a test boot, separate from the real server. The Datto Device can check if a machine has booted successfully and send a screenshot email to Business IT for verification. Any failed tests are diagnosed and details sent to Business IT for rectification
- Inverse Chain Technology – Datto’s proprietary technology that allows the most recent back on the Datto Device to be a fully constructed image of the protected server. Traditional backup solutions perform an initial “full system” backup and then records the incremental changes in a linked list. Restores from traditional systems can be lengthy, as the backups are compressed sequentially to build the recovery image. Inverse chain technology maintains each backup point as a fully constructed image that can be used in minutes.
- End-to-end Encryption – All data is protected by AES-256 encryption both in transit and while stored in the Datto Cloud. Data can also be encrypted locally on the Datto Device using a unique passphrase.
- Instant Virtualisation – Using Datto’s Inverse Chain Technology, the Datto Device can boot any snapshot of a protected server in minutes using the CPU and RAM on the Datto Device to host the virtual machine. The virtual machine will be available on the local network and normal business operations can continue with minimal disruption. Protected servers can also be virtualised in the Datto Cloud if the local Datto Device is not accessible.
- Ransomware Detection – Datto has developed a multi-tier ransomware detection process that searches the backup images for file encryption, bulk file changes, and other key indicators that a system is infected. If ransomware is detected, an alert is created and sent to Business IT for action. Customised Retention Periods – The Datto solution allows for flexible backup retention periods on the local Datto Device. Data retention has been set by Business IT to keep the local protected data until the storage capacity of the Datto Device is reached.
Secure User Support
Allspoke and if necessary, BIT are able to provide remote support services via the Connectwise client. Connectwise is a fast, secure remote support tool which is able to provide remote access with a much better piece of mind than products like VNC and Team Viewer.
This access can be provided upon request to customers to allow you to support your sites.